|
To add a new protocol type, click on the  button on the main screen toolbar. To edit the data of a type, select it in the main screen hierarchy and click on the button on the main screen toolbar. To edit the data of a type, select it in the main screen hierarchy and click on the  button. button.
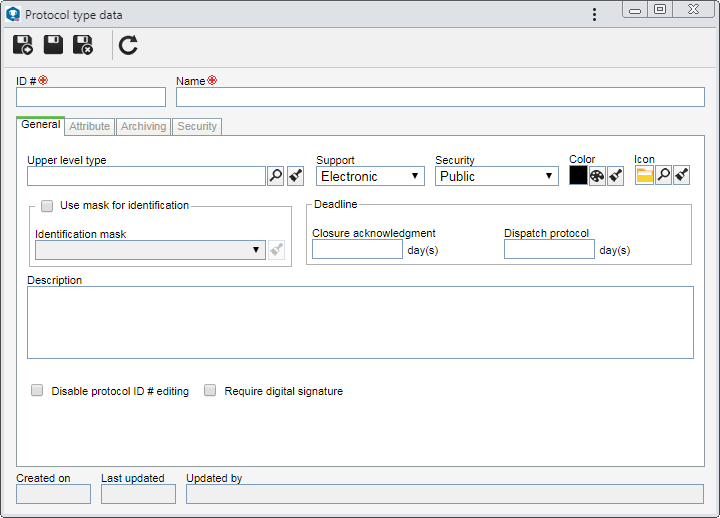
On the screen that will be opened, enter an ID # and a name for the protocol type. After saving the record for the first time, the following tabs will also be available:
Some of the features described below will only be available or work correctly if the SE Document component is part of the solutions acquired by the organization.
|
Field
|
|
Upper level type
|
Fill out this field for the protocol type to be hierarchically added below another type. In this case, select the desired protocol type. If a protocol type is selected in the main screen hierarchy, this field will be filled out by the system, but it will be possible to edit it.
|
Support
|
Define the document format that the protocol type will support:
▪Electronics: Documents with electronic files. ▪Physical: Documents with physical records. In this case, the "Archiving" tab will be enabled to fill out the necessary information. |
Security
|
Define who will have access to the information in this protocol type:
▪Public: Any user in the system. ▪Security list: Only users selected on the Security tab. ▪Participants: All participants involved in the protocol processing. |
Color
|
Select the color that will be used on the identification label of protocols from this type.
|
Icon
|
Select the image that will represent the protocol type on the screens in which the resource is used.
|
Closure acknowledgment (Deadline)
|
Enter the number of days the responsible party will have to confirm the acknowledgment of the closure of protocols of this type.
|
Dispatch protocol (Deadline)
|
Enter the number of days the responsible party will have to dispatch the protocols of this type. Thus, the "Deadline" field of the protocol dispatch screen will be filled out with the date resulting from the number of days set from the opening, and it will not be possible to edit it.
If this field is not filled out, it will be possible to enter a deadline when dispatching the protocol.
|
Description
|
Fill out this field to describe the protocols that will be classified in this type.
|
Option
|
Checked
|
Unchecked
|
Use mask for the ID #
|
When adding protocols to this type, the automatic identification resource will be used. To do that, in the respective field, select the desired identification mask.
|
The ID #s must be manually entered by the user who is starting the protocols of this type.
|
Disable protocol ID # editing
|
When starting a protocol of this type, it will not be possible to add or edit its ID #, regardless of whether it has been generated from a mask.
|
The ID #s generated for protocols of this type may be added or edited.
|
Require digital signature
|
All electronic files of the document must be digitally signed, so that the protocols from this type may have their processing finished.
In order for this feature to work correctly, it is necessary forr the proper configurations to be performed in the general parameters of SE Document and in the category of the documents related to the protocol.
|
It will not be required for the electronic files of the documents to be digitally signed to successfully finish the protocols of this type.
|
|
Use this tab to define attributes to complement the information of the protocols of this type. On the side toolbar, the following buttons are available:

|
Click on this button to associate an attribute with the protocol type. See how to perform this operation in the "Associating an attribute" topic below.
|

|
Click on this button to edit the default value and the controls of the attribute selected in the list of records.
|

|
Click on this button to save the association of attributes with the type.
|
|
Click on this button to disassociate the attribute selected in the list of records from the type.
|
Associating an attribute
|
To associate an attribute with the protocol type, click on the  button on the side toolbar. On the association screen that will be opened, perform the following steps: button on the side toolbar. On the association screen that will be opened, perform the following steps:
1.
|
Option
|
Checked
|
Unchecked
|
Restricted
|
The attributes that are selected in the list of records of the bottom part of the screen will be controlled. To do that, the following fields are also available:
▪Responsible: Click on the  button next to this field and, on the screen that will be opened, locate and select a team, organizational unit, department/position, position or user to have access to fill out the attribute values during protocol processing. Save the selection for this field to be filled out. button next to this field and, on the screen that will be opened, locate and select a team, organizational unit, department/position, position or user to have access to fill out the attribute values during protocol processing. Save the selection for this field to be filled out. ▪Type: This field displays the access type selected in the "Responsible" field. ▪Show attribute on report/label: oCheck this option so that the selected attributes are displayed in the reports and/or labels issued through the system. oIf this option is not checked, the selected attributes will not be displayed on the reports/labels issued by the system. |
The attributes that are selected in the list of records of the bottom part of the screen will not be controlled.
|
|
2.
|
 Use the filters to locate the attributes that will be associated more easily and click on the Use the filters to locate the attributes that will be associated more easily and click on the  button on the toolbar of the association screen to perform the search. button on the toolbar of the association screen to perform the search.
|
3.
|
According to the values entered in the filters, the attributes will be displayed in the list of records, located at the bottom of the screen. Select those you wish to associate with the protocol type. Hold the SHIFT or CTRL keys on the keyboard or check next to each record to select more than one attribute at a time.
|
4.
|
Fill out the following columns that correspond to the desired attributes as necessary:
Column
|
Default value
|
Enter a value that will be displayed already filled out in the attribute when protocols of this type are started.
|
R (Required)
|
▪Check this option so that, when starting protocols of this type, the completion of the attribute value is mandatory. ▪If this option is not checked, it will not be necessary to fill out the attribute to successfully start a protocol of this type. |
|
5.
|
After performing the necessary configurations, save the association. If changes are made to the attribute configurations (for example: an attribute previously checked as required is no longer required or vice versa), they will be replicated to the costs of this type when their data is edited.
|
|
|
This tab will only be available if the support set for the protocol type is "Physical". Use it to add the information about the archiving of protocols of this type.
Archiving type
|
Documents
|
Documents of this type will be archived document by document.
|
Archive folder/set of documents
|
The documents of this type will be archived in the form of a process (joined).
In the respective field that will be enabled, select the category to which the protocol will be added as a document. Notice that only the categories whose content type is "Process" will be available for selection.
|
|
Use this tab to define the security configurations for the protocols of this type. To do that, first perform the necessary settings in the Configurations section:
Option
|
Checked
|
Unchecked
|
Inherit security list from the protocol type (default)
|
The security list configured in this section will be valid for all protocols classified by this type. This option is displayed as checked by the system by default.
|
It will be possible to configure a specific security list for each protocol recorded in the type.
|
Block security change in the protocol
|
The "Inherit type security list" option cannot be unchecked when starting the protocol. With this, the security list set for the protocols in this section cannot be edited.
|
In the Security tab of the protocol data, it will be possible to check/uncheck the "Inherit type security list" option, as well as edit the security list.
|
Block record user editing
|
The "Record user" field will be filled out by the system and it will not be possible to edit it when starting the protocol.
|
The responsible for the protocol will be filled out by the system, but it will be possible to edit it.
|
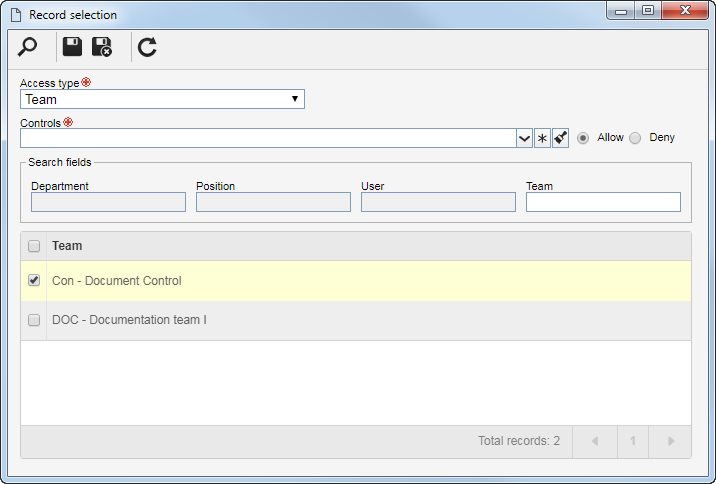
In the list of records at the bottom of the screen, it is possible to define a security list. To do that, click on the  button and, on the screen that will be opened, perform the following steps: button and, on the screen that will be opened, perform the following steps:
1.
|
Select one of the following options to set the access type that will make up the security list:
Access type
|
|
Team
|
It will be composed of the members of a team already registered in SE Protocol.
|
Organizational unit
|
It will consist of users of a particular business unit/department of the organization.
|
Department/Position
|
It will be composed of users from a specific department of the company, who have a specific position.
|
Position
|
It will be composed of users who hold a specific position in the company.
|
User
|
It will be composed of a specific user.
|
All
|
It will be composed of all users who have access to SE Protocol.
|
Addition user
|
It will be composed of the user who adds a protocol of this type.
|
Addition user department/position
|
It will be composed of users who belong to the same department or that hold the same position as the user who adds a protocol of this type.
|
Addition user position
|
It will be composed of users who hold the same position as the user who adds a protocol of this type.
|
Addition user department
|
It will be composed of users who belong to the same department as the user who adds a protocol of this type.
|
|
2.
|
According to the selected access type, the Search filters will be enabled to be filled out. Use them to make it easier to search for desired records.
|
3.
|
If the selected access type is Organizational unit, the hierarchy of business units and the departments belonging to them (if any) will be displayed.
Check the business units and/or desired departments. Next to the hierarchy, the system also makes available buttons that allow you to check all the sub-levels of a particular organizational unit or uncheck all sub-levels. Note that by using the "Check all sub-levels" button if new organizational sub-levels are subsequently added, they will not be included in the security list.
|
4.
|
 After entering the fields above, click on the After entering the fields above, click on the  toolbar button on the selection screen. Depending on the selected access type and the values entered in the filters, the result will be displayed in the list of records, located at the bottom of the screen. Select the ones that will compose the security list. Hold the SHIFT or CTRL keys down or check next to each item to select more than one record at a time. toolbar button on the selection screen. Depending on the selected access type and the values entered in the filters, the result will be displayed in the list of records, located at the bottom of the screen. Select the ones that will compose the security list. Hold the SHIFT or CTRL keys down or check next to each item to select more than one record at a time.
|
5.
|
In the Controls field, expand the list and check the desired actions. Then, define if they will be allowed or denied for the access type:
Control
|
Allowed
|
Denied
|
Add
|
The access type user will be able to start new protocols of this type.
|
The access type user will not be able to start new protocols of this type.
|
Edit
|
When the access type user selects a protocol of this type in the list of records, it will be possible to edit the data of this protocol.
|
When the access type user selects a protocol of this type in the list of records, it will not be possible to edit the data of this protocol.
|
Delete
|
When the access type user selects a protocol of this type in the list of records, it will be possible to delete this protocol.
|
When the access type user selects a protocol of this type in the list of records, it will not be possible to delete this protocol.
|
View
|
When the access type user selects a protocol of this type in the list of records, it will be possible to view the data of this protocol.
|
When the access type user selects a protocol of this type in the list of records, it will not be possible to view the data of this protocol.
|
Cancel
|
When the access type user selects a protocol of this type in the list of records, it will be possible to cancel/reactivate this protocol.
|
When the access type user selects a protocol of this type in the list of records, it will not be possible to cancel/reactivate this protocol.
|
Acknowledgment
|
The Closure acknowledgment task will be generated for the access type user.
|
The access type user will not receive the "Closure acknowledgment" task.
|
▪The controls that are not checked for a certain access type will be considered "denied". ▪Denied controls have precedence in the security list. For example: If Team A has permission to edit, and User B who belongs to this team has the edit control denied, User B cannot edit the record, even if they are part of a team with permission. ▪Use the other buttons next to the field to select all available controls and clear the checked options. |
|
6.
|
Once done, save your selection. Use the other side toolbar buttons to edit and delete the record selected in the security list.
|
|
After performing the necessary configurations, save the record again.
|







