|
By accessing the Configuration 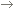 Authentication menu, the following sections will be displayed: Authentication menu, the following sections will be displayed:
In this section, it is possible to perform the configurations related to passwords and system logins. To do that, the following subsections are available:
Password control
Allows establishing controls regarding the passwords of system users:
Option
|
Checked
|
Unchecked
|
Request countersign when performing task1
|
The confirmation of the executor user countersign will be requested in the execution of the SoftExpert Suite component tasks.
|
The user may execute the SoftExpert Suite component tasks without the need for entering a countersign.
|
Request user countersign when performing critical operations in the components1
|
When executing operations such as deleting records, enabling/disabling records, and other critical operations, it will be required for the user to enter their countersign before the system executes it.
|
The user may perform deletions and other critical operations without the need to enter their countersign.
|
Allow users to request forgotten password
|
The login screen will display the "Forgot password?" option, so that the user can request it in case it has been forgotten.
|
The "Forgot password?" option will not be displayed in the login screen.
|
1 - For this feature to work correctly, users created in the system must have a countersign entered in their data screen.
Force users password change
|
This button should only be clicked if it is desired to change the passwords of all users registered in SE Suite. Thus, during the next login of each user, the system will request a password change.
|
Password strength
Use this section to configure the options that may make the user passwords stronger. As in every system, passwords are the first defensive line against unauthorized access. The stronger the password, the more protected the system will be. To do so, use the following options to define the mandatory requirements for the passwords of the system users:
Field
|
Filled out/Checked
|
Not filled out/Unchecked
|
Minimum size
|
Allows defining the minimum number of characters that the users must have in their password. When trying to create a password shorter than the minimum size, an alert message will be displayed warning that the minimum quantity of characters has not been met.
|
The passwords of system users will not have a minimum amount of characters.
|
Validity (months)
|
Allows defining the number of months for which the users are allowed to have the same password. Thus, when the deadline is reached, the users will be notified that their passwords have expired and a change will be requested.
|
The users may remain with the same password for an indefinite amount of time.
|
Repetition control
|
Allows defining the number of times the user must change their password before their old password can be repeated.
|
The users may change the password repeating an old password as many times as desired.
|
Upper and lower case characters
|
The passwords of system users must mandatorily have uppercase and lowercase letters.
|
It will not be mandatory for the passwords of system users to have uppercase and lowercase letters.
|
Special characters (for example: !, \$, #, %)
|
The passwords of system users must mandatorily have special characters (!, $, #, % etc.).
|
It will not be mandatory for the passwords of system users to have special characters.
|
Lock out user if the number of login attempts exceeds
This section must be used to configure the options to avoid unauthorized access from someone who is trying to guess the password of a system user. To do that, use the following fields:
Option
|
Filled out/Checked
|
Not filled out/Unchecked
|
Number of attempts
|
Allows establishing the number of attempts that the user can have to log in the system with an incorrect password before being blocked. To do that, enter the desired number of attempts, which can be from 1 to 5 times.
The user can be unblocked automatically (if the "Time for which the user will be blocked" field is filled out) or manually, through the Organization structure  User (AD004) menu in the SE Administration component. User (AD004) menu in the SE Administration component.
|
The user may try to log in with an incorrect password from 1 to 5 times.
|
Time for which the user will be blocked
|
Fill out this field to determine that, when a user is blocked for invalid login attempts, they are automatically unblocked after a certain period.
In this case, enter the number of minutes through which the user will remain blocked. Once the entered minutes are over, they will be automatically unblocked.
|
When a user is blocked for invalid login attempts, they must be unblocked through the Organizational unit  User (AD004) menu of the SE Administration component. User (AD004) menu of the SE Administration component.
|
Notify administrator
|
The system administrator user will be notified by email when a user is blocked due to invalid login attempts.
|
The administrator will not be notified when the user is blocked.
|
Several
In this section, several other options regarding user login are available:
Option
|
Checked/Filled out
|
Unchecked/Not filled out
|
Alert the administrator when any unknown login is identified
|
When a login attempt with an unknown user occurs, the system will email the administrator alerting about who tried to connect.
|
The system will not alert the administrator when there is a login attempt with an unknown user.
|
Block password change for users with simultaneous logins
|
The users configured to have simultaneous logins may not change their passwords through the "Account" menu in the suspended panel in the right side of the system main screen. In this case, users with simultaneous logins may change their password if they have access to the File  Organizational unit Organizational unit  User (AD004) menu of the SE Administration component. If they do not have access to this menu, only the system administrator may change the user's password through the same menu. User (AD004) menu of the SE Administration component. If they do not have access to this menu, only the system administrator may change the user's password through the same menu.
Note: The simultaneous login will be enabled if, in the user data, the "Max. number of connections" field is configured with a value greater than 1.
|
The users configured to have simultaneous logins may change their passwords through the Account. They may also change their password through the File  Organizational unit Organizational unit  User (AD004) menu of the SE Administration component, as long as they have access to it. User (AD004) menu of the SE Administration component, as long as they have access to it.
|
Block users creation
|
In the SE Administration component  File File  Organizational unit Organizational unit  User (AD004), the "Add" button will be displayed as disabled. It will only be possible to record users through integration with the LDAP server. User (AD004), the "Add" button will be displayed as disabled. It will only be possible to record users through integration with the LDAP server.
|
In the File  Organizational unit Organizational unit  User (AD004) menu of the SE Administration component, the "Add" button will be displayed as enabled, allowing the users to be recorded. User (AD004) menu of the SE Administration component, the "Add" button will be displayed as enabled, allowing the users to be recorded.
|
Idle timeout
|
Allows establishing the number of minutes for which the system can be idle, that is, without being used by the logged user. When the entered time is over, the user will be automatically disconnected and a message will be displayed requesting a reconnection.
|
The field needs to be checked and, once it is, it cannot be left empty. For users that do not have an inactivity timeout defined, the system will automatically determine that they will enter idle mode after 30 minutes.
|
Synchronize in login
|
The user will be synchronized as soon as they are authenticated This field must only be checked if one of the options for authentication with LDAP is enabled. Note that only the authenticated user will be synchronized.
|
If there is no LDAP authentication option configured, this field must not be checked.
|
|
External users
Option
|
Checked
|
Unchecked
|
Allow external users access to the system
|
Allows external users to access SE Suite through the URL displayed in the "Address for external users access" field. Use the Copy button next to the field to copy the URL and share it.
This way, the External user portal menu will be enabled to configure the operations the external users will be able to access and the information they will be able to view.
|
External users will not be allowed to access the system. Thus, the External user portal (CM030) menu will not be available to be configured.
|
External user self-registration
Option
|
Checked
|
Unchecked
|
Allow self-registration for external users
|
When a user accesses the External user portal through the link provided in the "Address for external users access" field, the Create account button will be displayed in the login screen, allowing the user to perform the registration.
In the License key field, select the license key that will be automatically assigned to external users who perform the self-registration.
|
External users can only be created by an internal user, through the File  External user (AD060) menu of the SE Administration component or the Contact section of a company data screen. External user (AD060) menu of the SE Administration component or the Contact section of a company data screen.
|
Require the approval of the self-registration of external users
|
When an external user self-registers, before access is granted, their registration must be approved through the File  External user (AD060) menu of the SE Administration component. External user (AD060) menu of the SE Administration component.
They can only access the External user portal after the approval.
|
The access will be granted to the external user after they confirm the registration through the e-mail that the system will send to the entered address.
|
▪For the confirmation e-mails to be sent correctly to the external user, it is necessary for the system to be enabled to send e-mails and for a valid e-mail server to be configured. ▪The configuration to assign a license key performed in this menu does not impact previously registered external users. |
|
In this section, it is possible to define how the authentication of users in the system will take place. To do so, in the Authentication mode section, check the desired option:
Option
|
|
Internal
|
Uses the standard SE Suite authentication, that is, the login and password configured in the user record.
|
NTLM v2
|
Allows the user to use the user code and operating system password to access the product. It uses the NTLM protocol to ensure communication security.
|
LDAP
|
Allows the user to use the user code and operating system password to access the product. It uses the LDAP protocol to ensure communication security.
|
SAML 2.0 (ADFS)
|
Indicated for scenarios in which the execution server, where SE Suite is being executed, and the LDAP server, which contains the user repository, are installed in different domains. Allows the user to use the 'Single sign-on' resource to access the product.
|
For more information on each authentication mode and which fits your company needs better, refer to the Authentication modes topic of the "Directory and authentication service" document.
|
The NTLM v2, LDAP and SAML 2.0 (ADFS) authentication types use an LDAP server to authenticate the users. Refer to the Configuration for direct directory service access of the "Directory and authentication service" document for more details on the configuration of this server.
|
|
This section will only be enabled if the "SAML 2.0 (ADFS)" authentication mode is checked. The configuration for authentication via SAML 2.0 (AD FS) consists of, basically, exchanging metadata files between the service provider (SE Suite) and the identity provider (AD FS). On the toolbar, the following buttons are available:
|
Click on this button to add a new configuration. See further details about this operation in the Configuring integrated authentication with SAML 2.0 (AD FS) topic of the "Directory and authentication service" document.
|

|
Click on this button to edit the configuration selected in the list of records.
|

|
Click on this button to delete the configuration selected in the list of records.
|
|
It is divided in two subsections:
Domains
This section will only be enabled if the "NTLM v2", "LDAP" and/or "SAML 2.0 (ADFS)" authentication modes are checked. The LDAP server configuration must be performed in it. In corporate environments with branches or rules divided by the department or position, many times there are LDAP servers distributed in a "forest". The token "forest" is used to identify an infrastructure made up of one or more domain trees.
Use the buttons below to configure the connection with multiple LDAP domains:
|
Click on this button to add a new LDAP connection. See further details on this operation in the Configuration for direct directory service access topic of the "Directory and authentication service" document.
|

|
Click on this button to edit the connection selected in the list of records.
|

|
Click on this button to delete the connection selected in the list of records.
|

|
Click on this button to disassociate users from the domain. Select the desired records before clicking on the button.
|
General options
Option
|
Checked
|
Unchecked
|
 Enable synchronization scheduling Enable synchronization scheduling
|
 The LDAP server synchronization scheduling will be enabled daily at midnight. This recurrence may be edited through the Monitoring The LDAP server synchronization scheduling will be enabled daily at midnight. This recurrence may be edited through the Monitoring  Scheduling menu. Scheduling menu.
|
 The synchronization will only be performed manually, by clicking on the The synchronization will only be performed manually, by clicking on the  button on the toolbar of the Authentication (CM008) screen. button on the toolbar of the Authentication (CM008) screen.
|
Accumulate department and position of the users
|
By performing the synchronization, the user departments and positions will be updated, without deleting the previous departments and positions.
|
Only the domain controller department will be maintained; the others will be unlinked from the user.
|
Log in automatically when integrated authentication is enabled
|
User sessions will be automatically started by accessing any page in the system, such as a link received via e-mail, for example. Thus, the login screen will not be displayed to type the credentials and the system will use the directory service authentication credentials, which were provided by the user when authenticating in the domain. The login screen will only be accessed if the entered URL is the specific page address, such as: https://example.softexpert.com/softexpert/login.*
|
When accessing a system URL, the login screen will be displayed, and after performing the authentication, the system will redirect to the requested page.
|
Enable license selection screen when logging in with single sign-on
|
This option must only be checked if Single Sign-On is enabled for use. Thus, when the user logs in, they must select the desired license. Only the licenses associated with the access groups related to the user will be available for selection.
|
The user will access the system with the license from the last access. The user may edit the license after the login through the "Edit license key" menu on the suspended panel on the right side of the main screen of the system.
|
Enable logout with single sign-on
|
This option must only be checked if Single Sign-On is enabled for use. Once the user logs out, the system will delete their session.
|
After logging out, the user session remains active.
|
Enable integrated authentication for users that are not synchronized
|
Enables Single Sign-On even without integration with AD. This parameter must be performed when it is necessary to import users in a way other than via direct integration with AD, as Single Sign-On (SAML) can work without this integration. If this parameter is enabled, a domain to synchronize AD users must not be registered, as it can cause conflicts in Single Sign-On.
|
Only synchronized users will have Single Sign-On enabled.
|
*By accessing the default system URL (or any other system URL), without having the user authenticated in the directory service, an authentication page from the domain controller can be displayed, depending on the infrastructure configurations performed. If the user has the credentials for service authentication, they can provide it and the service will then direct them to the SE Suite page. If they do not have a directory service login, or have not had access to the domain controller login page, it is recommended to access it by the SE Suite login URL. It may be necessary to type the credentials in the login screen when:
▪It is necessary to access the system with the administrator user (admin); ▪The user does not have directory service credentials and only accesses it through an internal user in the system; ▪The system has been accessed through a network without access to the directory service and other protocols are allowed, such as NTLMv2 or LDAP. |
|
This section displays the history of the user synchronizations made in the system. It is possible to view the synchronization start and end date and time, its status (Executing, Executing with errors, Loading AD information, Loading SE Suite users, Comparing the users of SE Suite with the users of AD, Calculating permissions of users, Finished and Finished with errors), the number of processed records, with permission and with errors. In order to track a synchronization that is being performed, click on the  button to update its status. button to update its status.
The "Calculating permissions of users" status indicated that new users are being added and the system is creating the access permission structure for them. This step may take long depending on the number of new users. The progress of the user permission processing may be tracked in the "With permission" column. The statuses that display errors refer to users with lack of information, invalid formats or conflicting information, and the reason for the error can be seen in the import details.
To view the details of an import (users with error, updated users, imported users and disabled users), select the history record and click on the  button. To view more details on the possible errors the synchronization process may display and how to solve them, refer to the Errors that can occur in user synchronization topic of the "Directory and authentication service" document. button. To view more details on the possible errors the synchronization process may display and how to solve them, refer to the Errors that can occur in user synchronization topic of the "Directory and authentication service" document.
Use the  button to delete the record selected in the list of records. button to delete the record selected in the list of records.
|
This section displays the history of the team synchronizations made in the system. It is possible to view the synchronization start and end date and time, its status (Executing, Executing with errors, Loading AD information, Loading SE Suite users, Comparing the users of SE Suite with the users of AD, Calculating permissions of users, Finished and Finished with errors), the number of processed records, with permission and with errors. In order to track a synchronization that is being performed, click on the  button to update its status. button to update its status.
The "Calculating permissions of users" status indicated that new teams are being added and the system is creating the link to the users. This step may take long depending on the number of new teams and users to be linked to each team.
To view the details of an import (teams with error, updated teams, imported teams and disabled teams), select the history record and click on the  button. button.
Use the  button to delete the record selected in the list of records. button to delete the record selected in the list of records.
|
This section will display the records of the simulation and synchronization processes of SE Identity (except for records previous to the time set in the audit configurations). It is possible to identify the application installation location and the network address of the computer in which it was installed, as well as the application version and other information regarding the executed process. If any errors that stop the initialization of the synchronization/simulation process occur, the record status will indicate "Error" and its details may be viewed by selecting the record and clicking on the  button. button.
|
After performing the desired configurations, save them.
|







