
Correction of vulnerabilities
General vulnerabilities ▪Update of the third digit version of Java Tomcat to fix a security failure known as "Ghostcat"; ▪Update of the PHP version used in the product for version 7+, given that the previous version (5.6) was obsolete and no longer received update packages against vulnerabilities; ▪Correction of several features previously susceptible to SQL Injection and XSS (Cross-site Scripting), which are vulnerabilities in which an ill-intended user tries to manipulate parameters in the request to obtain unauthorized access to system data or data of other users, or even perform operations without the proper permission; ▪Correction of several features previously susceptible to Local File Inclusion, which is when an ill-intended user tries to force the upload of an arbitrary file, such as a file from the server operating system instead of the official application file; ▪Disabled the use of PHP functions that execute commands in the operating system, such as exec() and system(), as they are unnecessary commands for the application and, by disabling them, third-parties are prevented from inadvertently creating a security breach in the system; ▪Improvements in the validations related to the user sessions to ensure that it will not be possible to access protected features without the proper permissions. ▪Some information on login and environment have been moved to memory storage to avoid making them available in the workspace. Such information is now recovered only if it must be used by the system. |
Countersign confirmation for critical operations
Aiming at ensuring information security, a configuration has been created in the system to require the confirmation of the user countersign when they try to perform an operation considered critical or sensitive to the product.
This new configuration is an evolution of the previous option, which required the countersign only when opening the activity execution screens. From now on, with the new configuration enabled, the confirmation of the user countersign will be ensured for a much wider range of operations, such as deletions, releases, revisions, publications and others.
To have this additional security in the product, simply enable the new option in the system authentication configuration screen (CM008). The option is "Request user countersign when performing critical operations in the components".
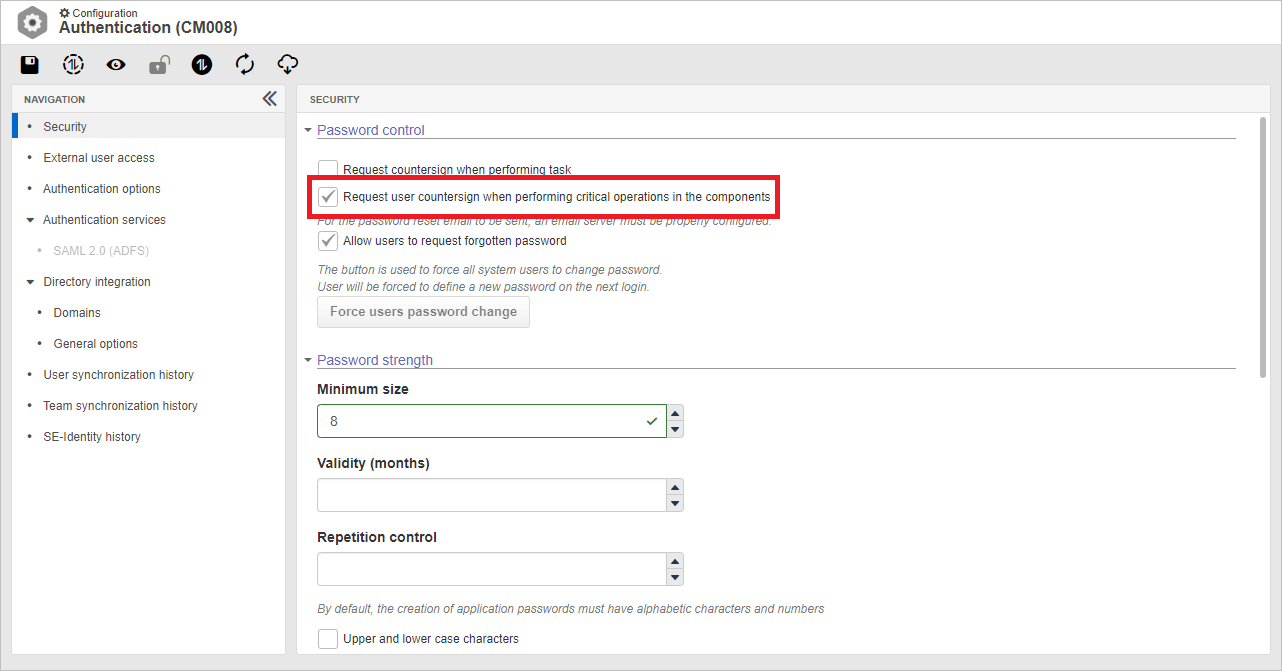
Note Only one of the countersign confirmation configurations can be enabled, since the new option is an evolution of the previous one. Thus, we recommend using the new option, which ensures confirmation in critical operations, as it provides an additional security layer that is far superior to the one provided by the previous option. |
Full text search configuration menu (CM032)
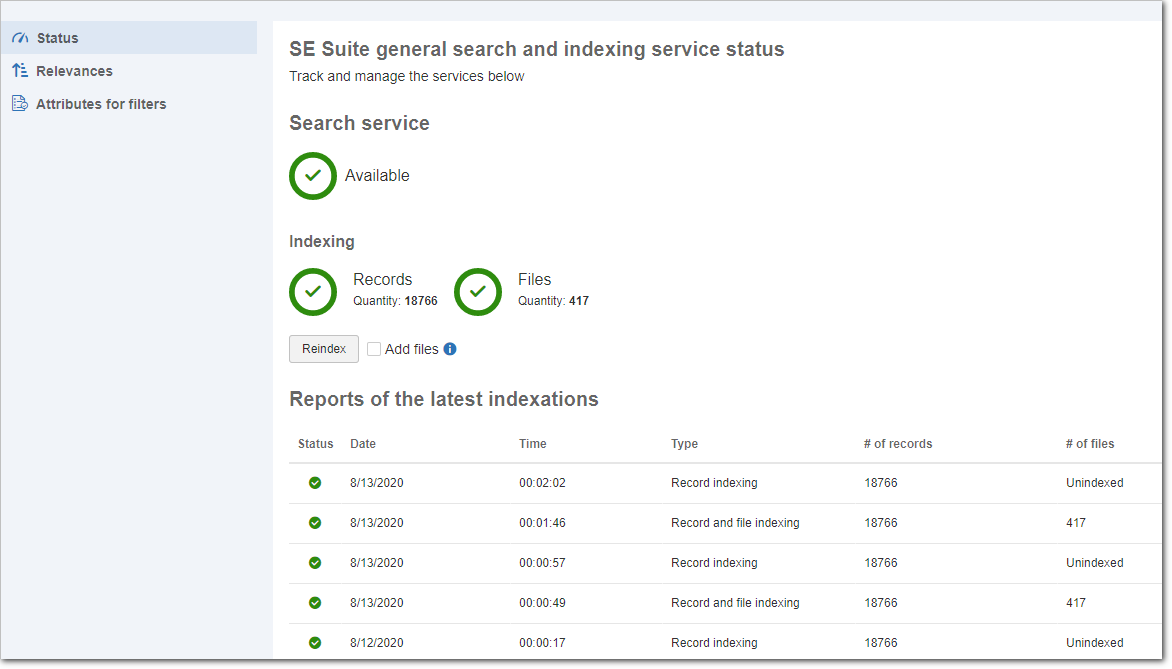
This new screen has been created for system administrators to have higher control over the behavior of the SE Suite full text search, and it has three tabs: "Status", "Relevances" and "Attributes for filters". In the "Status" tab, it is possible to check the availability of the search service and a list of the indexings performed. Moreover, in extreme cases, with guidance from SoftExpert, it is possible to manually trigger the indexing process.
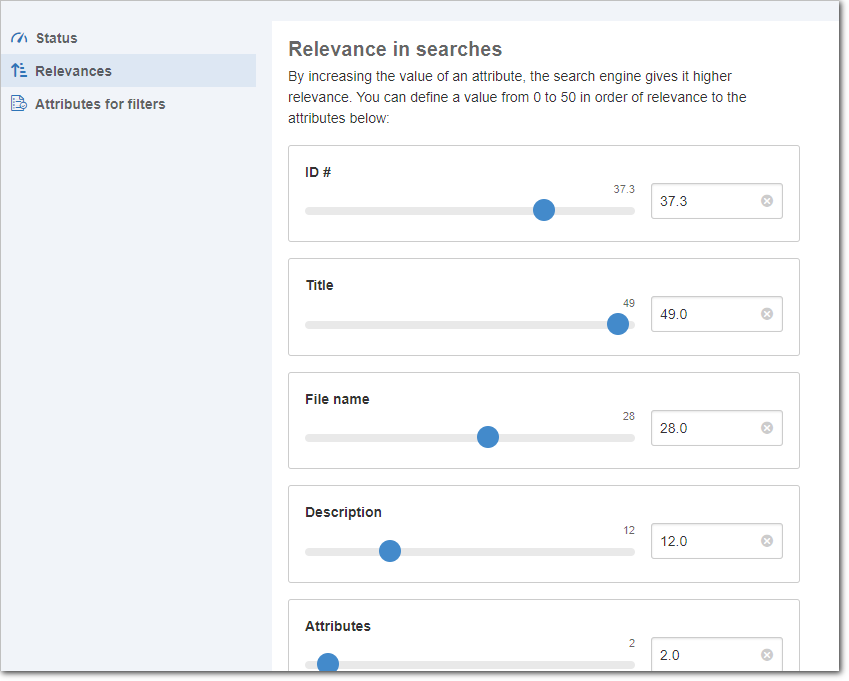
In the "Relevances" tab, it is possible to increase or decrease the relevance given by the full text search to each of the criteria taken into consideration in the search. This change impacts searches for all users, so it must be made carefully and thoughtfully.
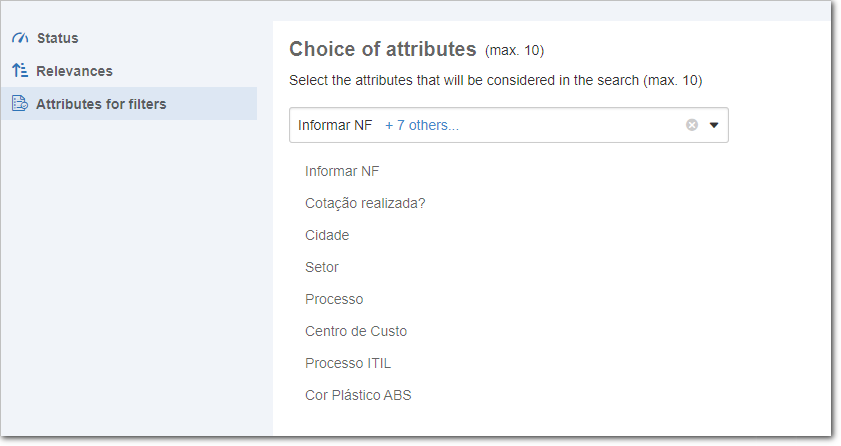
Finally, in the "Attributes for filters" tab, it is possible to maintain a list of attributes that will be available as filters for refining the search.
They appear in the search results as follows:
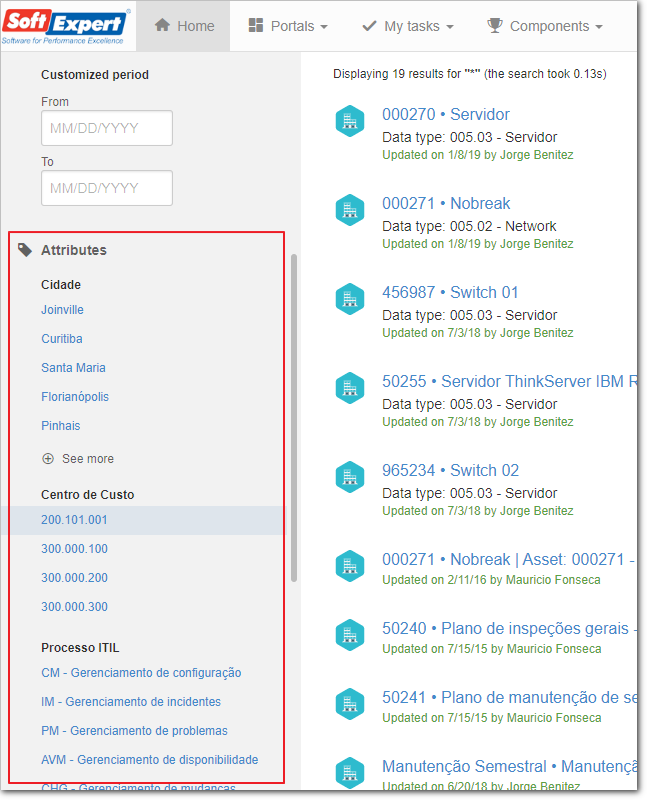
Time for which the user will be blocked
An option has been created to allow configuring the time for which the user will be blocked after exceeding the limit of invalid login attempts.
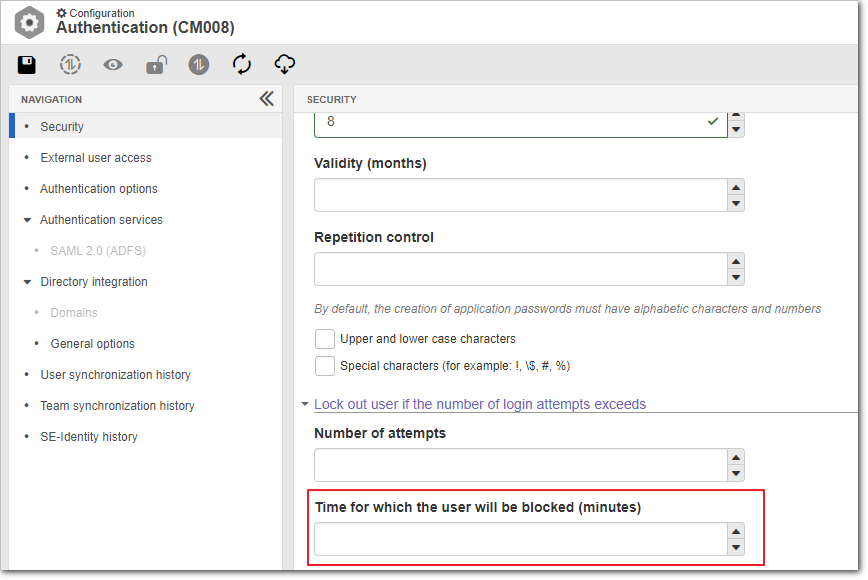
External user self-registration
An option was added to allow external users to self-register to access SE Suite. To do that, it is necessary to select a default license key for these users and choose whether there will be internal approval for them.
Recommendation: Avoid using Office365 as e-mail server
Alert for the use of Office365 as e-mail sending server. Microsoft limits the number of sent e-mails and recommends the use of specialized providers to mass send e-mails, according to this quote from their official website:
Exchange Online customers who have to send legitimate bulk commercial email (for example, customer newsletters) should use third-party providers that specialize in these services. (https://docs.microsoft.com). |
Previous versions
View also the improvements made to this component in previous versions:
