|
In this section, it is possible to configure the security list of the type and requests classified by it. See below, how to configure each sub-tab:
1.
|
By default, the system preconfigures that all users have access to the request of the type in question, however, this configuration can be edited. In the following steps, the system will display how to add a new access control in the list and these steps are also valid for editing the access control configured by the system.
|
2.
|
 To add a new access type, click on the To add a new access type, click on the  side toolbar button and fill out the fields of the following screen that will open: side toolbar button and fill out the fields of the following screen that will open:
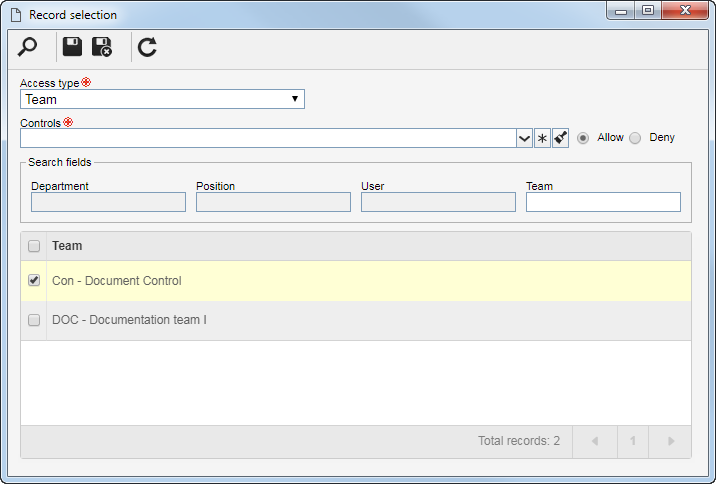
|
3.
|
In the Access type field, select one of the following options to set the access type that will make up the security list:
Control
|
|
Team
|
It will be composed of the members of a team previously created in SE Request.
|
Department
|
It will be composed of users from a certain department of the organization.
|
Department/Position
|
It will be composed of users from a specific department of the company, who have a specific position.
|
Position
|
It will be composed of users who hold a specific position in the company.
|
User
|
It will be composed of a specific user.
|
All
|
It will be composed of all users who have access to SE Request.
|
|
4.
|
According to selected access type, the Filters will be enabled to be filled out. Use them to facilitate the search of users who will form the security list.
|
5.
|
 Then, click on the Then, click on the  toolbar button of the selection screen. Depending on the access type selected and the values entered in the filters, the result will be displayed in the list of records, located at the bottom of the screen. Select the ones that will compose the security list. Hold the SHIFT or CTRL keys down or check next to each item, to select more than a record at a time. toolbar button of the selection screen. Depending on the access type selected and the values entered in the filters, the result will be displayed in the list of records, located at the bottom of the screen. Select the ones that will compose the security list. Hold the SHIFT or CTRL keys down or check next to each item, to select more than a record at a time.
|
6.
|
In the Controls field, expand the list and check the desired actions. Then, define if they will be allowed or denied for the access type:
Control
|
Allowed
|
Denied
|
Add
|
The user will be able to issue requests of this type.
|
The user will not be able to issue requests of this type.
|
Edit
|
The user will be able to edit the data of the requests of this type.
|
The user will not be able to edit the data of the requests of this type.
|
Delete
|
The user will be able to delete requests of this type.
|
The user will not be able to delete requests of this type.
|
View
|
The user may view the request data screen in "read-only" mode.
|
The user will not be able to view the data of the requests of this type.
|
Cancel
|
The user will be able to change the status of requests.
|
The user will not be able to change the status of the requests of this type.
|
Print
|
The user will be able to generate reports related to the requests.
|
The user will not be able to generate reports of the requests of this type.
|
▪The controls that are not checked for a certain access type will be considered "denied". ▪Use the other buttons next to the field to select all available controls and clear the checked options. |
|
7.
|
After setting the necessary configurations, save the selection.
Use the other side toolbar buttons to edit and delete access controls of the security list.
|
|
1.
|
To configure the security list of the type, first, select one of the following options:
▪Public: Any SE Request user will have the access permission to the type. ▪Restricted: Only determined SE Request users will have the access permission to the request type. When selecting this option, the side toolbar buttons will be enabled. Click on the  button and fill out the following fields on the data screen that opens: button and fill out the following fields on the data screen that opens:
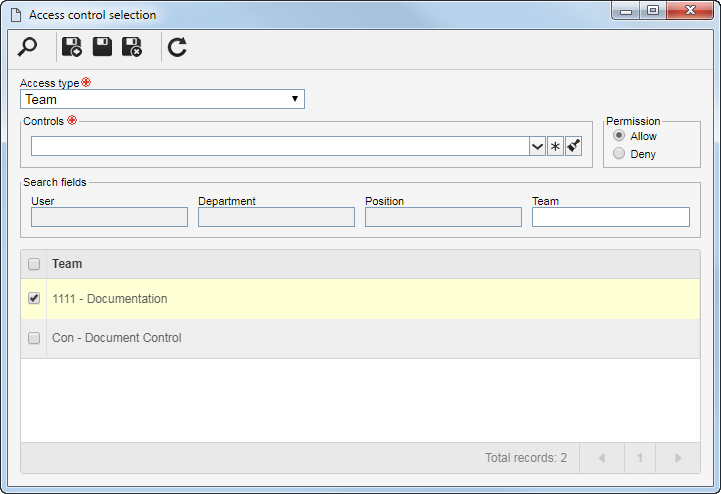
|
2.
|
In the Access type field, select one of the following options to set the access type that will make up the security list:
Access type
|
|
Team
|
It will be composed of the members of a team previously created in SE Request.
|
Organizational unit
|
It will consist of users of a particular business unit/department of the organization.
|
Department/Position
|
It will be composed of users from a specific department of the company, who have a specific position.
|
Position
|
It will be composed of users who hold a specific position in the company.
|
User
|
It will be composed of a specific user.
|
All
|
It will be composed of all users who have access to the SE Request component.
|
|
3.
|
According to selected access type, the Filters will be enabled to be filled out. Use them to facilitate the search of users who will form the security list.
|
4.
|
If the selected access type is Organizational unit, the hierarchy of business units and the departments belonging to them (if any) will be displayed. Check the desired business units and/or departments. When checking the "Consider sublevels" option at the bottom of the screen, the system will also consider the organizational units that are down in the hierarchy of the selected organizational unit. Note that by checking this option, if new organizational subunits (whether they are business units or departments) are subsequently added, they are automatically added to the security list. Next to the hierarchy are also available buttons that allow you to check all sub-levels of an assigned organizational unit or uncheck all sub-levels. It is important to note that by using the "Check all sub-levels" button if new organizational sub-levels are subsequently added, they will not be included in the security list.
|
5.
|
 Then, click on the Then, click on the  toolbar button of the selection screen. Depending on the access type selected and the values entered in the filters, the result will be displayed in the list of records, located at the bottom of the screen. Select the ones that will compose the security list. Hold the SHIFT or CTRL keys down or check next to each item, to select more than a record at a time. toolbar button of the selection screen. Depending on the access type selected and the values entered in the filters, the result will be displayed in the list of records, located at the bottom of the screen. Select the ones that will compose the security list. Hold the SHIFT or CTRL keys down or check next to each item, to select more than a record at a time.
|
6.
|
In the Controls field, expand the list and check the desired actions. Then, define if they will be allowed or denied for the access type:
Control
|
Allowed
|
Denied
|
Add
|
The user will be able to add new types to the levels below the type in question.
|
The user will not be able to add subtypes to the type in question.
|
Edit
|
The user will be able to edit the type data.
|
The user will not be able to edit the type data.
|
Delete
|
The user will be able to delete the type.
|
The user will not be able to delete the type.
|
Security data
|
The user will be able to edit the configurations performed in the Security tab of the type.
|
The user may edit the other data of the type, but the "Security" tab will remain blocked.
|
List
|
The type will be displayed for the user in the system screens that have document type hierarchy.
|
The type will not be displayed for the user in the system screens that have document type hierarchy.
|
View
|
The user will be able to view the type data screen in "read-only" mode.
|
The user will not be able to view the type data.
|
The controls that are not checked for a certain access type will be considered "denied".
|
|
7.
|
After setting the necessary configurations, save the selection.
Use the other side toolbar buttons to edit and delete access controls of the security list.
|
|
|







