Correction of vulnerabilities
General vulnerabilities ▪The addition of arbitrary PHP files, sent via upload to the temporary file application folder as valid system files, has been blocked. In other words, a Local File Inclusion vulnerability that could lead to Remote Code Execution of other PHP codes has been fixed. ▪"CSV Formula Injection" vulnerability fixed when exporting view screens to Excel. ▪Improvements based on good safety practices (security through obscurity) ▪Source map removed from Javascript codes, which facilitated the understanding of the application frontend logic. ▪The JavaScript code was hidden on the login screen to hinder the understanding of the frontend logic on this screen, as it is public (able to be accessed by unauthenticated users) and it has sensitive logic, such as that for password recovery. ▪JavaScript functions that exposed the name of backend technologies have been renamed to hinder the discovery of which technology is used in the application and which resources use a certain technology. |
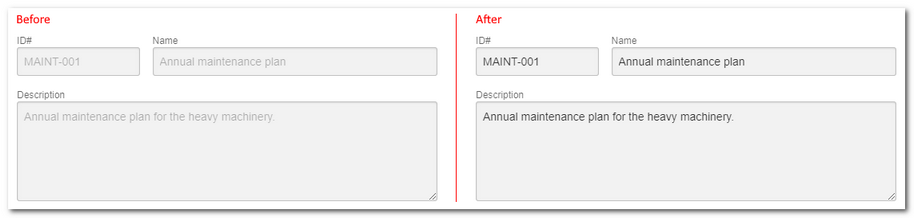
Improvement in text contrast in disabled fields
On some screens, the text on disabled fields had an inadequate gray shade, as it provided low contrast and made it harder for users to read the content.
From this version onwards, the color has been changed to a darker shade, increasing contrast and readability of the text in disabled fields.
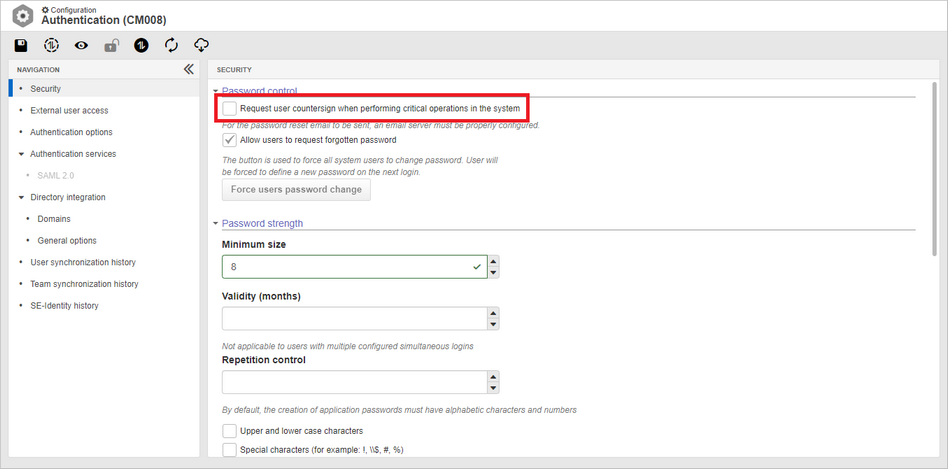
Old countersign confirmation option hidden
The new "Request user countersign when performing critical operations in the system" parameter was created in version 2.1.3 to replace the old parameter, which only required the countersign confirmation to open the task screen, but both options continued existing since, so that there was enough time to adapt to the migration between options.
After the adaptation time, the objective now is to make the old option obsolete, so, from this version onwards, it will only remain available in the environments in which it is already enabled. Otherwise, only the new option will be displayed, and it will no longer be possible to enable the old option.
In the near future, the old option will be completely discontinued and it will no longer work, so it is recommended for those who still use it to plan the migration to the new option created in version 2.1.3.
oAuth authentication in the SMTP e-mail server
To be in compliance with the SMTP servers in the market and to provide greater security in connections, the oAuth authentication method is being made available when registering e-mail servers.
Update of the indexing service - ElasticSearch
Aiming to constantly improve the search service, the ElasticSearch indexing service is being updated to version 7.10.
This version has some performance improvements and a solution to some files that occasionally generated errors during the indexing.
Avoiding problems of too many bytes per row in dynamic entities
An improvement has been made to decrease the maximum number of attributes and references to avoid problems of too many bytes per row in dynamic entities.
Disabling generic users
Due to security matters, some users with generic logins and with reserved words were disabled and are blocked from being enabled.
In previous versions, the creation of those users had already been blocked. Examples of blocked users: softexpert, sesuite.
End of life
Below is a calendar of the support termination for the following requirements:
▪Oracle 12 (all versions): 2.1.9 - October 2022
▪Windows Server 2008 R2: 2.1.10 - December 2022
▪Windows Server 2012 (all versions): April 2023
▪SQL Server 2012 (all versions): April 2023
Previous versions
View also the improvements made to this component in previous versions: